The NICTER project conducts researches on the vulnerabilities of IoT devices, as well as observations of those exploitations. Recently, we found a new attack method that exploits the DDNS feature of ASUS routers and their management app ‘ASUS Router App’ to acquire router credentials. We formally reported this vulnerability to ASUS.
In response, ASUS published an advisory on July 25, 2023, titled ‘Strengthening DDNS Security for RT-AX1800U, RT-AX3000, RT-AX3000 v2, RT-AX86U, TUF-AX3000 and TUF-AX5400’.
As of December 2023, it is estimated that over one million routers worldwide are at risk of being affected by this issue. If attacked, the router’s credentials (username and password) could be unauthorizedly obtained by attackers. However, it is very difficult for users to directly confirm if their credentials have been stolen. Therefore, indications of a security breach can only be detected indirectly, such as noticing unauthorized changes to router settings.
This article aims to reiterate the countermeasures and introduce an overview of the attack method.
Additionally, this issue was presented at Black Hat Europe 2023 recently held in London. The presentation slides are available, and those who wish to gain a deeper understanding of this issue are encouraged to refer to them as well.
Affected Routers
The advisory published by the vendor lists models such as RT-AX1800U, RT-AX3000, RT-AX3000 v2, RT-AX86U, TUF-AX3000, and TUF-AX5400. However, it’s important to note that not just these models, but all ASUS-manufactured routers managed using the ASUS Router App may potentially be affected by this attack.
Affected Users
Attackers can intercept communications from the app by altering the DDNS entry (IP address) of the target router to their own IP address. This enables them to unauthorizedly access the router’s credentials.
Therefore, users who meet the following conditions are at a higher risk of being attacked:
- Using the ASUS Router App with the ‘Remote Connection’ feature enabled1 2
- Using an outdated version of the ASUS Router App
- Launching the ASUS Router App using an internet connection other than their home WiFi
Countermeasures
As of December 2023, ASUS’s DDNS system does not require an authentication process and can change IP addresses using only the MAC address and the tareget FQDN. Therefore, there is a risk that users unintentionally connect to an attacker’s IP address when launching the ASUS Router App. As it is difficult for users to completely prevent this type of attack, the following countermeasures are recommended:
- Change the router’s password
- Avoid using the ASUS Router App
- Disable the ‘Remote Connection’ feature on the router
- Use a web browser to access the router’s management interface via LAN and configure the router settings
It has been confirmed that logging into the router using the latest version of the ASUS Router App changes the DDNS domain name generation algorithm, automatically updating to a domain name that is difficult for third parties to guess.
However, there is still a possibility that the credentials have already been leaked and the router has been compromised by attackers. As the Tokyo Metropolitan Police Department’s warning3 states, it’s important to check for any suspicious configuration changes. If unfamiliar settings are found, it is recommended to reset the router, update the firmware to the latest version, and perform initial settings without using the ASUS Router App.
Details
The main reasons for the success of the attack are the discovery of multiple specification issues and vulnerabilities in the router, app, and DDNS server.
- The DDNS domain name is generated using the MD5 hash of the MAC address, which makes it easy for attackers to guess
- The change of the IP address registered on the DDNS server can be executed with just the MAC address and domain name, and there are open-source tools available that make this easy to do4
- Although TLS is used for the connection from the app to the router, there is no verification of the certificate, making it impossible to detect impersonation by attackers
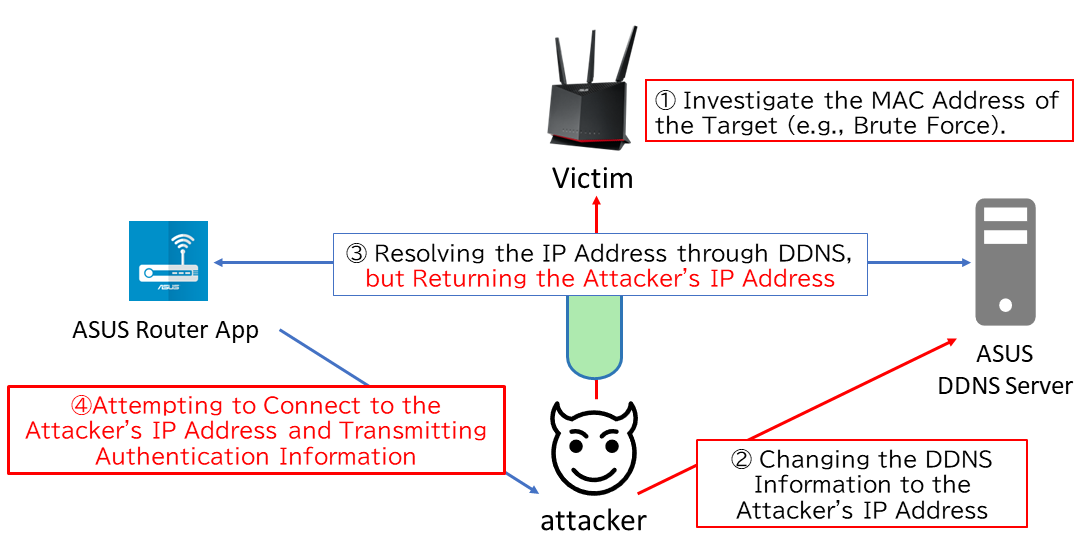
The attack method for unauthorizedly accessing router credentials by combining these specifications and vulnerabilities is demonstrated in the following steps:
- Identify the DDNS domain name from the MAC address of the target router
- Change the IP address of the identified DDNS domain to the attacker’s IP address
- When the user launches the ASUS Router App, the DDNS server performs name resolution and returns the attacker’s IP address
- The user’s device automatically attempts to connect to the attacker’s IP address, and during this process, the router’s credentials, encoded in Base64, are also transmitted
As a result, attackers are able to obtain the router’s credentials by decoding the Base64-encoded data. Using these obtained credentials, they can log into the target router and take control of the user’s network by changing settings such as the SSH server or VPN server/client.
Conclusion
In this case, there is an issue that it’s difficult for users to realize they have been attacked. Therefore, it is strongly recommended for users of ASUS routers to regularly check their router settings. However, such measures alone are not sufficient to completely prevent attacks. Not limited to this ASUS case, it is advised for all internet-connected devices to avoid unnecessarily exposing their management interfaces on the internet. If they need to be exposed, it is recommended to implement measures such as restricting the IP addresses that can connect.
-
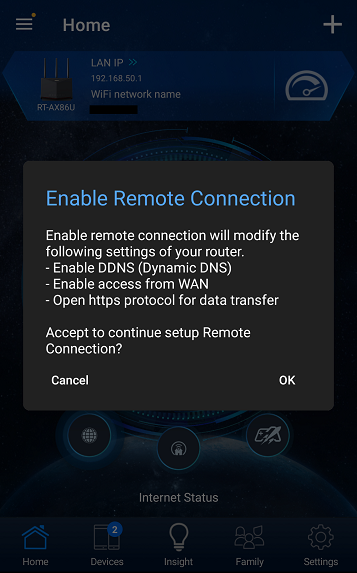
When initial router settings are configured using the ASUS Router App, pressing ‘OK’ on the confirmation screen shown as Figure 1 after completing the settings will automatically activate the ‘Remote Connection’ feature. Consequently, it is highly possible that a significant number of users may unintentionally enable this feature ↩︎
-
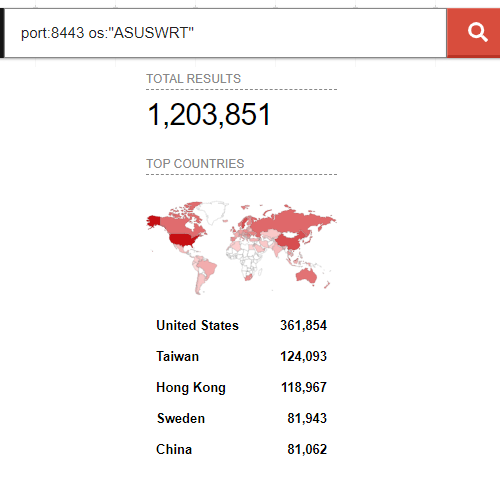
The Shodan search result shows that a large number of ASUS-manufactured routers with their management interfaces exposed on the internet exist. This indicates that some of the prerequisites for the attack are present in many hosts. ↩︎
-
https://www.keishicho.metro.tokyo.lg.jp/kurashi/cyber/notes/router.html ↩︎